Nothing could’ve prepared modern businesses for what 2024 already brought forth: cybersecurity threats, a widespread talent shortage, and the never-ending tech evolution. But what do all these challenges have in common? You guessed it – secure remote access – and here’s why:
- To tap into a broader talent pool, cut costs, or offer flexibility as a top employer, remote access will become a norm sooner rather than later.
- As remote work and Bring Your Own Device (BYOD) practices become more popular, they bring both opportunities and challenges in maintaining security.
All in all, the need for secure remote access solutions is already critical. Don’t get us wrong, this technology is great. It allows employees to connect to company systems from anywhere, without compromising security.
So, it’s time to explore why secure remote access is the future of any digitalized business and prepare you to adopt it the right way. That’s why we’ll also discuss its key components, including virtual private network, MFA, and endpoint security.
How Does Secure Remote Access Work?

In 2023, 72 percent of global respondents showed concern about the online security risks of employees working remotely. Clearly, there’s a lot to consider when switching to a remote workforce. The implications of cyber-proofing secure connections or risking your organization’s data are significant.
There’s hope, though. Secure remote access means you can control access to networks, systems, and confidential data. Here’s how it works:
Step 1: Authentication and authorization
In simple terms, authentication means validating the identity of users and their devices through credentials like usernames, passwords, biometrics, or security tokens. Authorization means giving role-based access control to determine the level of application access granted. Ensuring secure access means granting access to only the resources people require in their work.
In addition to standard user authentication, privileged access management (PAM) plays a crucial role in ensuring secure remote access. PAM focuses on securing access to privileged accounts and resources, such as administrator accounts, which have advanced privileges and control over critical systems.
Step 2: Encrypted connections and secure pathways
After authentication and authorization, secure remote access establishes encrypted connections between users and target systems (e.g. the corporate network). Encryption converts data into a code that can only be deciphered with the correct decryption key. So, even if unauthorized third parties try to intercept it, the data remains unreadable.
To further strengthen security, strong remote access solutions employ secure pathways, such as VPN tunnels or SSL connections, under which remote sessions (e.g., RDP, SSH, SQL) are tunneled to prevent interception and unauthorized access.
The Virtual Private Network and Zero Trust Network: remote access solutions you should know

VPNs (Virtual Private Networks) create a secure tunnel between remote devices like mobile devices and your network. They encrypt data to boost network security and prevent unauthorized access and interception during remote connections.
In 2022, nearly six out of ten respondents stated that their company planned on improving the authentication of their current VPN.
Additionally, organizations are starting to consider Zero Trust Network Access (ZTNA). ZTNA is a relatively new security model that assumes no trust, even within your network (e.g. the internal corporate network). Zero-trust network access verifies users even further. It analyzes the identity and the security context of every user and device accessing corporate resources.
ZTNA relies on the following factors to grant access on a per-session basis:
- User identity
- Device security status
- Other context and security posture factors (e.g., location, time of access)
Step 3: Real-time monitoring and session management
Secure remote network access solutions record all session activities as video files, allowing you to review sessions. This way, admins can block access or terminate suspicious sessions and receive alerts on anomalous activities.
Audit logs and session data connect with Security Information and Event Management (SIEM) systems to improve threat detection and response.
Key Components of a Secure Remote Access Solution
Secure remote access is essential for organizations to allow remote users entry while facing security challenges. Key components include:
1. Multi-factor authentication (MFA)

Multi-factor authentication (MFA) helps boost security, as it requires more than just a password to allow access to a network. It involves a set of credentials you know (like a password) with something you will receive through authentication (like a code sent to your phone) or even using a biometric factor (like using a fingerprint or facial recognition). Studies show MFA can reduce successful cyberattacks by up to 99.9%.
2. Endpoint security and device management
Endpoint security refers to protecting individual devices (computers or mobile devices), from cyber threats like malware and viruses. Solid antivirus software is essential here, as it scans for and removes malicious software.
Additionally, device management tools in endpoint protection are crucial in monitoring device activity or applying security patches and updates.
3. Network Access Control (NAC)

Network access control determines who and what can gain access based on security policies. These solutions authenticate and authorize devices before allowing them to enter your network, so that only trusted, healthy devices are granted access.
4. Single sign-on (SSO)
Single sign-on (SSO) simplifies the login process while ensuring robust security. It helps users access multiple applications and services with just one set of credentials.
Benefits of Implementing Secure Remote Access
Now, let’s tap into the five most important benefits of using secure remote access for your business.
1. Increased productivity and flexibility for remote workers

Some say the future of work is remote. We think that it’s more of a present reality. It’s not unheard of to see a sales executive closing deals from a coffee shop or a project manager collaborating on the go.
“Without RealVNC remote access software we wouldn’t be able to multitask as much as we do today in IT .” – Shearvon Devenish, Information Systems Manager
- Outsourcing employees is good for business. Eventually, the outsourcing market is projected to reach $525 billion in 6 years.
- Employees demand new benefits, including flexible schedules, hybrid work, and the possibility to work from remote locations.
- Happy workers mean more productive workers – and that’s a given.
2. Enhanced security for corporate networks and sensitive data
Robust access controls and encryption protocols enhance secure remote access and safeguard your corporate networks. Implementing strict access controls, verifying user identities, and allowing only healthy devices to securely access your network fortifies protection against cyber threats.
For example, tools like RealVNC Connect offer a simple, secure, and ready-to-use remote access and support solution for organizations demanding strong security and reliability.
3. Reduced risk of data breaches and cyber attacks
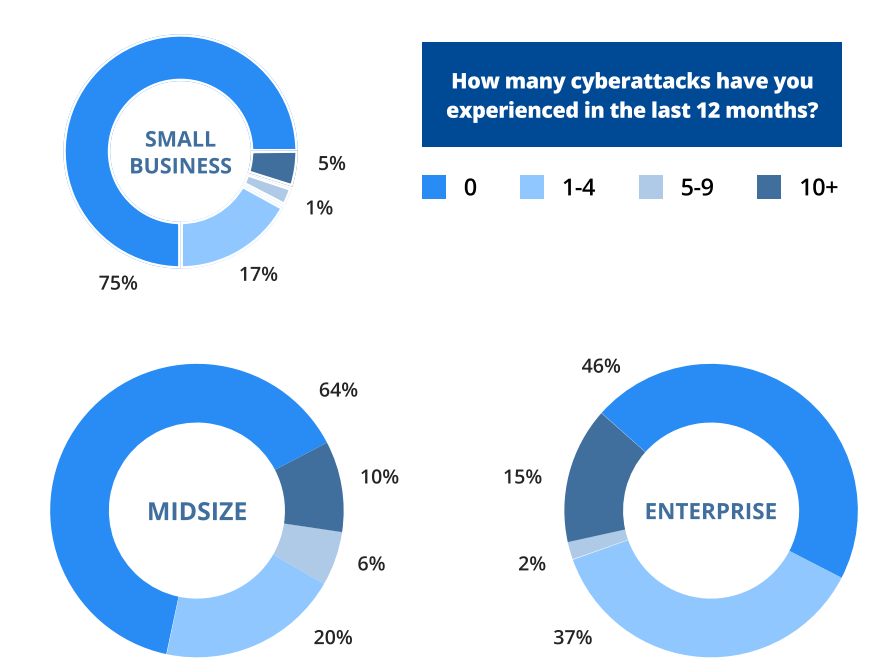
While larger organizations usually experience more cyber attacks, no company is spared from cyber threats.
Secure remote access can reduce the risk of data breaches and cyber-attacks if used correctly. That means implementing proactive security measures, like VPNs or zero trust network access (ZTNA). On top of these security hygiene practices, vetting authorized users and teaching employees about security protocols is essential.
4. Cost savings through BYOD policies and reduced office space requirements

If you’re looking to optimize costs, a BYOD (Bring Your Own Device) policy is a great approach to consider. When employees are responsible for their own devices, you’ll save on costs like purchasing and maintaining business hardware. Also, you can consider investing in application infrastructure instead.
5. Improved business continuity and disaster recovery capabilities
In times of crises, secure remote access means your business operations run uninterrupted. In turn, this enhances disaster recovery capabilities. When employees work remotely, you can maintain productivity and service delivery, even during emergencies.
Best Practices for Secure Remote Access
With the ever-rising threats in the cyber landscape, make sure to go through the following checklist for best practices to secure remote access management:
1. Develop and enforce strong security policies:

- Create detailed security policies on remote work protocols, data handling procedures, and the right way to use devices on and off company premises.
- Work on crafting guidelines on how to safely access corporate networks. Consider implementing requirements for VPN usage, tips on how to secure private or public Wi-Fi connections, and manage data encryption.
2. Regular employee training
- Conduct training sessions covering various cybersecurity topics (phishing attacks, email spoofing, malicious attachments, modern data breaches, and best password protocols).
- Conduct simulations of real-world cyber threats.
3. Implement strong authentication methods
- Deploy multi-factor authentication (MFA) across all remote access points to add an extra layer of security beyond passwords.
- Use single sign-on (SSO) solutions to simplify user authentication processes.
- Encourage the use of long, complex passwords or passphrases combined with multi-factor authentication (MFA) and the use of password managers.
4. Monitor and log remote access activities:

- Implement logging mechanisms from a centralized source to track remote access activities and detect odd behavior in real time.
- Use security information and event management (SIEM) systems to aggregate and analyze log data for threat detection.
5. Keep software and security solutions updated
- Use automated patch management to improve the patching process and minimize the risk of exposure to known vulnerabilities.
- Conduct regular vulnerability assessments and penetration testing. Enable automatic updates for operating systems, applications, and security software.
Why Choose RealVNC for Secure Remote Access?
Hackers are getting smarter by the day, constantly coming up with new ways to break into our systems. Whether it’s through phishing emails or sophisticated malware, they’re always looking for vulnerabilities to exploit, especially in remote users.
Consider all the sensitive information your business handles every day — from customer data to trade secrets. A breach in your cybersecurity could mean losing customers’ trust, facing legal trouble, and dealing with financial losses.
That’s why staying secure online isn’t just a nice-to-have — it’s essential.
To face all your secure remote access management challenges like a pro, choose a reputable 360-degree solution like RealVNC. We provide strong encryption, secure authentication, and solid access controls to protect remote connections. Sign up for your free trial today.
Frequently Asked Questions
How do I create secure remote access?
To create secure remote access, you can implement strong authentication methods like multi-factor authentication (MFA) and complex passwords. Then, use encryption to protect data during transmission, and enforce strict access controls to allow only authorized users and devices.
How do I secure my remote connection?
Secure your remote connection by using a virtual private network (VPN) or Zero Trust Network Access (ZTNA) solution. Ensure encryption of data in transit and implement strong authentication methods like MFA. Another obvious yet crucial tip is to update software and educate remote users on security practices.
Which remote access protocol is considered secure?
VPN and ZTNA are both secure remote access protocols. VPNs create a secure tunnel between the user’s device and your network, while ZTNA focuses on verifying the identity and security parameters of the user and device before granting the person safe access to connect remotely.
What is secure remote working?
Secure remote working involves accessing business resources and application access from outside the traditional office environment. The key to secure remote working is ensuring confidentiality, integrity, and availability of information in the most secure way for the company and the users. This requires using security measures like encryption, authentication, and access controls.
How does remote access improve productivity for remote and hybrid workers?
Remote access boosts productivity by allowing your employees to work from anywhere, anytime. Think of internationally distributed teams collaborating at all times, less commuting time, flexibility in work hours, and so much more!
What are the key considerations when choosing secure remote access solutions?
When choosing secure remote access solutions, consider factors like ease of use, scalability, compatibility with existing infrastructure, and adherence to industry standards. Consider a holistic solution for your secure remote access needs, such as RealVNC. Its commitment to security, including end-to-end encryption and granular access controls, cross-platform compatibility, ease of use, and scalability features, make it a top choice for organizations of all sizes.
How can organizations ensure secure remote access for BYOD devices?
Organizations can ensure secure remote access for BYOD devices through mobile device management (MDM), endpoint security solutions, network access control (NAC), and secure remote access gateways.
What are the potential risks of unsecured remote access, and how can they be mitigated?
Unsecured remote access poses risks such as data breaches or malware infections from cyber threats like phishing attacks, which can target a weak link or new employee, and then spread to your organization’s applications and infrastructure. To mitigate these risks, you should implement security best practices, such as those discussed in this article.