They are the most commonly used access control elements of digital security architecture, but also the most vulnerable.
According to Verizon’s 2019 Data Breach Investigations Report (DBIR), 80% of hacking-related breaches involve compromised and weak credentials – this same figure was given in the 2017 DBIR report, and indicates that it’s still a problem worth talking about. Hackers with criminal intent exploit the poor password practices of the masses, and can use existing passwords and creation patterns to model user routine, deducing new passwords based on past formats.
So why are passwords vulnerable? The main reason is the fact that they don’t actually provide any information on the unique identity of the user. Passwords can be shared around and exploited by anyone who gets a hold of them, whether they have consent or not. The security level of a password also lies in the hands of the account holders, often opting for easy-to-remember words and phrases over unique strings of numbers, symbols and odd characters. All too often, users trade off strength for convenience, just closing the latch without locking the deadbolt.
The fallible nature of humans can explain why more and more organizations are implementing two-factor authentication (2FA) or even multi-factor authentication (MFA) to tighten their security and provide greater protection from cyber-attacks.
How does multi-factor authentication work?
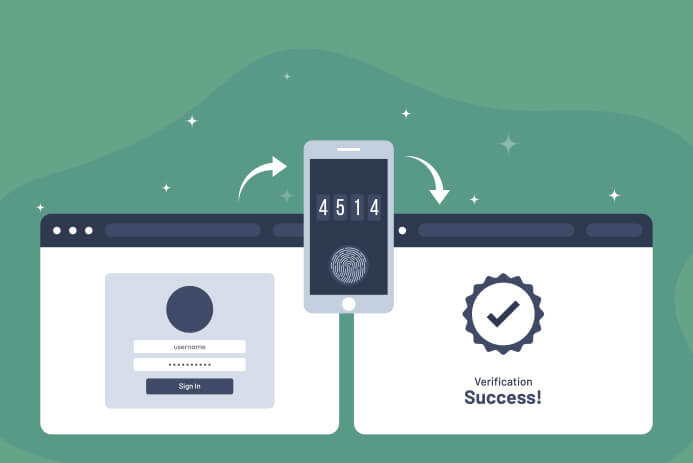
Multi-factor authentication (MFA) is a more secure access control procedure that combines multiple credentials unique to an individual to verify the user’s identity. A MFA combination involves two or more of the following credentials:
- Something the user knows – this could be a password, PIN, or the answer to a security question
- Something the user has – a device, a smart card, a key fob etc.
- Something the user is – a voice, a fingerprint, maybe even an iris scan?
The additional layers of verification in MFA means that even if one of the authentication factors is compromised, anyone trying to obtain illegitimate access is impeded by further obstacles. For example, if a password is compromised for any reason, the account cannot be breached without further credentials.
So what are the two factors used in two-factor authentication? The first one is usually something the user knows – a password for an online account, or the PIN to a credit card. The second factor can be anything the user has or is – a text to a device, a physical card, a fingerprint, or any of the other options listed above (and more!).
Given the nature of remote access activities, security is of paramount importance, and MFA adds a very strong additional defense to any criminal attacks. It should be a mandatory part of any enterprise remote access strategy.
Read more: How to remotely access another computer
Two-factor authentication vs multi-factor authentication
The most commonly used form of multi-factor authentication is two-factor authentication (2FA), probably because it’s the simplest way to add an extra layer. 2FA is currently available for most social media platforms and SaaS business applications, as well as for many offline services. If you think you’ve never used 2FA, think again – have you ever withdrawn cash from an ATM? You have the card, you have the PIN – two factors to authenticate your access to the money in a specific account. Most online services will ask for two digital authentication factors, such as a password and a code sent as a text to a linked personal device. MFA and 2FA’s differences are minute in terms of factors and layers of authentication. 2FA is actually just a subset of MFA – all 2FA are MFA, but not vice-versa. Each additional authentication factor provides a further level of security.
Using 2FA is the first step towards a fully secure software stack, and should be the absolute minimum required when it comes to accessing business-critical systems. Multi-factor authentication is then the next logical step when you’re taking security to the next level.
Multi-factor authentication helps support compliance
Regardless of what you are using it for, remote access system implemented in an environment with industry regulations to meet should comply, or support compliance with those regulations. Currently, many compliance standards specifically mandate the use of multi-factor authentication across all devices. In most cases, even when using MFA is not specified, it is still best practice when aiming to meet security requirements demanding a strong and well-defined security architecture.
For example, to be compliant with the Payment Card Industry Data Security Standard (PCI DSS), any accounts with access to any systems handling cardholder data must be secured by MFA.
Failing to meet compliance standards can be catastrophic for an organization, causing loss of trust and reputation, disruption to business, and significant fines.
Are the benefits of MFA worth the hassle?
Multi-factor authentication systems offer many essential security benefits, but they do come at a small price. End users can find them awkward, often needing to re-authenticate on a regular basis. This can quickly become burdensome with additional authentication factors, making simply logging onto a system time consuming.
Despite the potential inconvenience to end users using MFA for remote access, we strongly recommend using MFA where possible, and believe that the benefits vastly outweigh the costs. The uptick in cyber crime over recent years means that relying on a combination of usernames and passwords alone for business-critical services presents an extremely high security risk that organizations cannot afford to take.
Unfortunately even the most complex, randomly-generated passwords aren’t safe enough, and can be snatched by hackers through phishing attacks and data breaches. While no security system is fool proof, MFA provides essential additional layers of security to protect an organization against cyber crime.
Looking for a remote access solution with multi-factor authentication, up to 256-bit AES encryption, and support for industry compliance standards? Take a free trial of VNC Connect, and see why millions of users trust our service for their remote access needs.