As much as we’d like to think we’re rid of it, externally exposed RDP remains alive and well (for some unknown reason). And that’s a HUGE problem for those organizations that are relying on it. Don’t get me wrong; there’s nothing wrong with using RDP – it’s the insecure use of RDP (no MFA, no monitoring, older host OSes, one-off exposed systems that everyone forgets about, etc.) that is the creates the risk for the organization.
And it’s such a huge problem that RDP’s misuse by cybercriminals continues to make it into reports on the current state of cyberattacks. Take the Quarterly Ransomware Reports from ransomware response vendor Coveware – they’ve been continuously covering various stats about the ransomware attacks (including initial attack vectors) that they respond to for their customers since 2018. RDP was listed in 2018 as an initial attack vector (it was #1) and it’s still on the board in 2023 just behind email phishing but ahead of vulnerabilities.
So, how is RDP actually used within cyberattacks (ransomware or otherwise)? At a high level, we can look at Sophos’ 2023 Active Adversary Report for Tech Leaders, where we get a bit of a deeper breakdown:
- RDP played some role in 95% of attacks, up from 88% in 2022
- Internal use of RDP was seen in 93% of attacks, with external use seen in 18% of attacks
- RDP was used only for internal access and lateral movement in 77% of attacks
We can gather from this data that RDP is used as both an initial means of entry into an organization’s network, as well as a means to move laterally within the compromised network. This alone should be enough justification to make you think to yourself “OK – it’s time to ditch RDP”.
But, what really happens when threat actors gain control over an exposed endpoint via RDP?
Generally, we need to speculate based on the end result of an attack and determining of what transpired from forensics evidence. Rather than do that, we now have the results of an unprecedented three-year long RDP honeypot study by security vendor GoSecure where more than 20,000 RDP sessions were monitored, and 190 million threat actions were collected using a custom-built interception tool that recorded over 100 hours of RDP session footage, in order to answer this question.
What 5 Types of Threat Actors Do With a Compromised RDP Session
To make 20,000 sessions worth of threat actions digestible (and, apparently, to express the inner Dungeons & Dragons, or “D&D” nerd within some of us!) the kind folks at GoSecure categorized the activities into 5 types of D&D character classifications:
- Rangers – In D&D, rangers are a skilled explorer, craftsperson, and hunter. GoSecure found that these types of threat actors run reconnaissance using scripts or tools, explore the contents of the compromised system, and check the performance of the system. The going theory is that they are evaluating the system for another type of threat actor; this could be indicative of an initial access broker who simply sells the credentials and resulting remote system access.
- Thieves – In D&D, thieves are, well… thieves. They burgle, steal, pickpocket, etc. All-round bad guys. GoSecure characterizes these threat actors as those intent on monetizing the simple RDP access gained without going beyond the “walls” of the compromised endpoint. Actions include installing cryptominers, proxyware, monetized browsers, etc.
- Barbarians – In D&D, barbarians thrive in battle. Threat actors of this nature are the ones who love the thrill of hacking the rest of your network. They are the ones discovering IP address ranges, finding usernames and passwords/hashes/Kerberos tickets, etc. in an attempt to brute force their way into more computers on your network.
- Wizards – In D&D, wizards are highly skilled at performing spells (and they usually have no real combat ability), accomplishing the impossible without explanation (i.e., “magic”). GoSecure sees threat actors that use RDP to “portal” (read: laterally move) from system to system. These may be the most skilled of all the threat actors, as wizards are very skilled at living off the land and are able to laterally move with relative ease.
- Bards – Bards in D&D are sort of a “jack of all trades”, part musician, part fighter, part wizard. In general, though, they are also in the “master of none” category. According to GoSecure, bards have “no apparent hacking skills”; they misuse the compromised RDP session for far more personal needs that include downloading movies, watching porn and performing web searches related to hacking.
So, what’s the breakdown of these five types of threat actors? Are they all just watching movies? Laterally moving? Running cryptominers?
According to a BlackHat 2023 presentation by GoSecure cybersecurity researchers on their findings of this three-year experiment, the activities are heavily weighted towards barbarians and rangers:
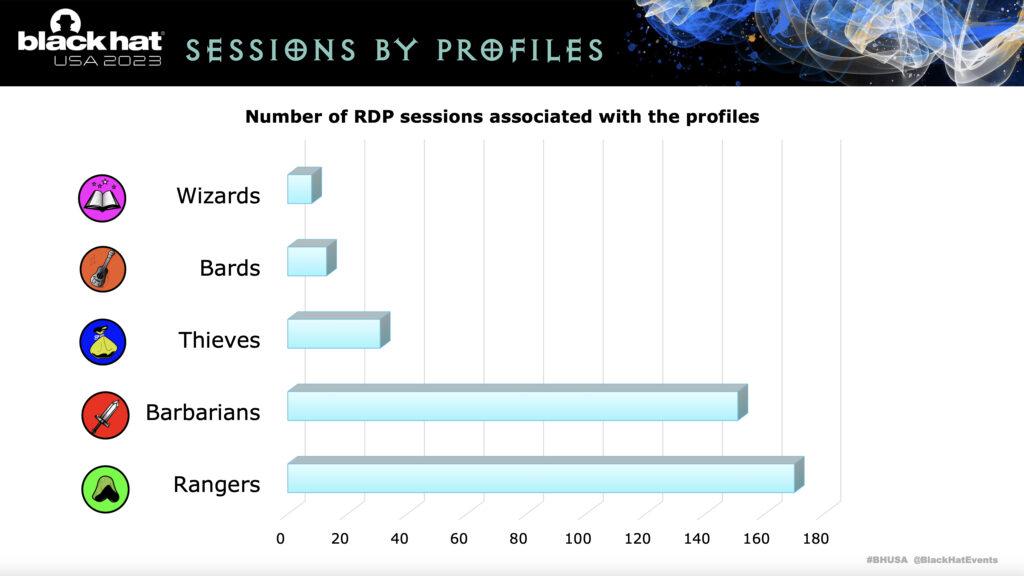
While I’m unsure of the scale used, it’s still very evident that barbarians and rangers combined dwarf thieves, bards, and wizards. This means that, for most RDP sessions, the name of the game is reconnaissance and lateral movement. To give you a bit more insight into the kinds of actions taken, GoSecure researchers also classified the tools used by all categories of threat actor:
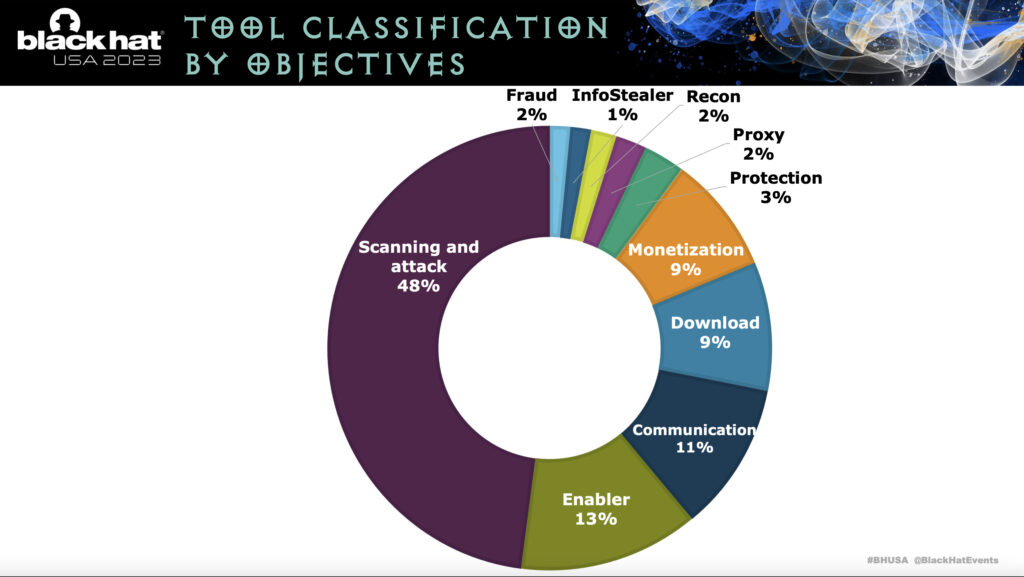
You can establish from this tool classification that actions involved with cyberattack far outweigh any of the other types individually. Again, RDP is seen primarily as a channel for attack.
Moving Away from RDP – Both Inside and Out
If the industry data wasn’t enough to move you, I’m hoping the GoSecure detail was! It’s evident that insecure RDP is a risk to the organization, both as an externally accessible means of entering a network and as a means to move laterally throughout a compromised environment.
Assuming your organization has a need for both external and internal remote access, what should you do to mitigate this risk entirely?
The answer lies in using a means of secure remote access that includes a few controls in place before anyone is allowed to remotely access anything:
- Multi-factor authentication – it’s 2023; everyone (and I mean everyone) should have MFA enabled on their user account. If you have MFA layered over remote access, you put initial access brokers largely out of business.
- Granular Access Control – RDP, if left unchecked, allows anyone to jump to any other machine (yes, yes, you need Log On Locally rights, etc., but you get the point!). Secure remote access limits who can utilize remote sessions to specific machines.
- Least Privilege – RDP sessions leverage the permissions of the logged-on credential. Secure remote access can often determine what level of privileges are exercised in a given remote session.
In all reality, implementing a secure remote access solution that had any of these features would be an improvement in reducing the risk. Why? Because RDP is built-in (and the threat actors know it!) and completely removing RDP and utilizing another more secure solution would be another barrier for a threat actor to overcome.
If you have any instances of RDP within the organization, it’s time to eradicate them completely and look for another means of securely providing remote access – whether externally or internally – that removes the threat actors’ easy means of remotely existing within your network. To ignore this warning brings new meaning to the phrase “barbarians at the gate.”













