There’s no doubt that the days of the classic office are behind us. Working remotely allows your employees to have greater flexibility while maintaining their productivity levels and remote desktop access is one tool that supports the modern workplace.
Remote access allows your employees to work from home while ensuring that they still have access to the desktops used in the office. The productivity benefits are obvious, however, you also must be aware of the cybersecurity and compliance challenges.
When adopting remote desktop access, you must remain compliant with data privacy and security regulations. With customer and employee data security covered by stringent regulations such as GDPR, HIPAA, CCPA, and more, it’s crucial that you don’t allow your remote access systems to open up vulnerabilities in your data privacy policies.
Fortunately, it’s possible to maintain accessibility for your remote employees while keeping your network secure—read on to find out how.
What is remote desktop access and why could it pose a challenge for your IT security?
If your company uses a remote working system, then remote desktop access and other remote access tech should be part of your IT risk assessment matrix, but what do we mean when we say remote desktop access?
Well, imagine that you want to access some files stored on your work desktop from the comfort of your home office—remote access is what enables you to do this. This has been around for a while (remote desktop access was first included with Windows in 2001), but the recent increase in working from home has meant that more organizations are relying on this technology.
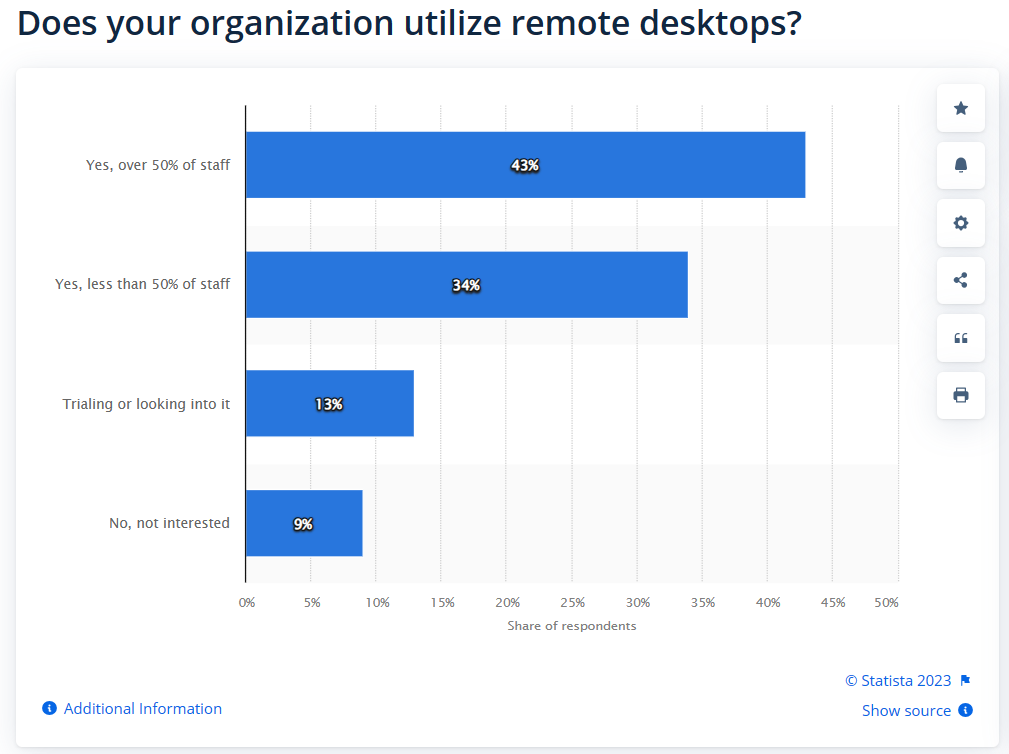
You’ve probably heard of Remote Desktop Protocol (RDP). It’s the de facto technology for remote access in Windows. RDP means that your employees are able to access their desktops from anywhere in the world, letting them work just as if they were in the office.
However, RDP’s default settings weren’t designed for the type of large-scale use that many organizations are implementing as they transition to a world of working from home. Without extra protections, remote desktop access can open your network and databases to cyberattacks.
All of this means that using remote access can risk your organization’s data security. If your remote desktop access is running on an unsecured network, for instance, anyone using that network could potentially have access to your data. In an age of stringent privacy regulations, this could have significant consequences.
How to make sure that your remote desktop access is secure
Despite the cybersecurity risks that can come with remote desktop access, if you want to have a flexible and modern organization it’s not an option to stop using remote access technology.
So, how can you set up safeguards to ensure that your employees are accessing your networks safely and securely?
1) Use Multi-Factor Authentication
Multi-Factor Authentication (MFA) ensures that employees can only access their accounts after they’ve confirmed their credentials through an app or by verifying their identity with an email or through their mobile number.
At first, MFA can seem frustrating or time-consuming, but you can mitigate this by only requiring verification once a week or every time that an employee uses a new device. Any interference, however, is worth it—MFA is the best way to make sure that you really know who is using your network through remote access.
2) Connect via secure networks

As much as you might want to do your work at the nice coffee shop down the road, it’s much safer to use remote desktop access on networks that you know are fully secure. This can include home WiFi networks, wired internet connections, or a 4G/5G connection.
Connecting remotely via public WiFi is a common mistake. Anyone else on the network may be able to intercept any data that you’re sending while working. It’s imperative that you only use secured networks if you want to ensure compliance when using remote desktop access.
3) Consider using a VPN
Despite this, there is a way to use public WiFi networks securely: By using a remote access VPN. You should think of a VPN (a Virtual Private Network) as a tunnel through which any data that you send and receive travels, thus hiding it from anyone else on a WiFi network.
VPNs will not only encrypt your data but also mask your IP address. Using one will make it much more difficult for potential hackers to access your data when working remotely.
4) Keep your software and hardware up-to-date
Cybersecurity is a constantly evolving battle, with developers continually responding to new threats and vulnerabilities. Software updates almost always include security patches, while it’s also crucial that your hardware uses the latest drivers to overcome any security vulnerabilities.
Any device that you use for remote access must use the latest software. You can use compliance auditing software to keep tabs on your software and make sure that you’re always up-to-date.
5) Monitor access
One of the most important principles for any organization that uses remote access is to always ensure that you know who’s using your network.
Login attempts should be logged, while you should also stay on top of user behaviors so that any unusual activity can be recognized and responded to.
6) Use strong passwords and encryption
If all of your employees are using ‘’password’’ as their passwords, you shouldn’t be surprised if your data is breached.
You should encourage your workforce to use strong passwords, including numbers and special characters, on any device that they use to remotely access your network.
As well as this, another basic practice that can vastly improve your security for remote desktop access is encryption. Protection against data interception will never be perfect, so making sure that all of your data is encrypted will make it much more difficult for hackers to read or use your data.
7) Implement firewall protection
Another fundamental part of any remote access policy is the use of firewalls. These are essentially barriers that can filter any threats that enter an internal network.
This means that you can use a firewall to make sure that any incoming traffic, such as via a remote desktop, is vetted, preventing any unauthorized access.
As well as this, most modern firewall software comes with advanced cybersecurity measures such as malware protection. Using firewall protection is one of the best ways to use remote access safely.
8) Move on from RDP
As we highlighted earlier, RDP is one of the classic ways for organizations to use remote access. However, there are many examples of man-in-the-middle attacks (where a hacker secretly intercepts data) that exploit the weaknesses in RDP, while it is also vulnerable to malware attacks.
To protect yourself against these threats, it’s best to use a more up-to-date remote access solution that places greater importance on the cybersecurity of large organizations.
There is a good choice of such solutions, and you should take time to find the one that best suits your company’s requirements. For instance, VNC Connect is remote access software that works securely across multiple platforms.
9) Train your staff

Of course, all of these practices would be useless if your employees aren’t aware of them or choose not to follow them. You must emphasize the risks that come with using remote desktop access so that they take care to protect themselves against its vulnerabilities.
Remote access tools, such as the software that your organization uses to enable employees to connect from home, should be introduced with extensive training.
As well as this, you should educate all of your employees about how to spot phishing scams—there are usually tell-tale signs that can protect you from this form of hacking.
Training should be a continual process. Cyberthreats evolve over time and employees should be regularly updated about how to spot the latest problems. Having a well-informed workforce can act as a human firewall on top of the technical solutions that are an integral part of ensuring compliance for remote desktop access.
Keeping remote desktop access secure in the future of work
In our digital age, more and more organizations are becoming ever more reliant on digital technology and data. At the same time, however, we’re also becoming unshackled from the office. This combination has meant more employees are using remote desktop access.
This means that it’s never been more important to ensure that remote access is fully compliant with data privacy policies and regulations. While software such as RDP brings with it a number of cybersecurity challenges, it’s possible to use remote access securely.
You can achieve this in your organization by following the practices in this article, including using secure networks, encrypting your data, choosing fully secure remote access software, and using firewalls and VPNs. All to ensure compliance in the age of remote desktop access.













